 On the 11th of October, ICANN will implement the most impactful change since the adoption of DNSSEC in the root zone back in 2010:. They will replace, or “roll over”, the key signing key (KSK) for the first time since the signing of the root zone eight years ago. While the DNSSEC protocol foresees in regular roll-overs, the reality is that not all DNS resolvers and ISPs are ready yet when it comes to a root zone roll-over. Though the majority of all resolvers are updated correctly, some users may experience nonfunctional websites from the 11th of October.
On the 11th of October, ICANN will implement the most impactful change since the adoption of DNSSEC in the root zone back in 2010:. They will replace, or “roll over”, the key signing key (KSK) for the first time since the signing of the root zone eight years ago. While the DNSSEC protocol foresees in regular roll-overs, the reality is that not all DNS resolvers and ISPs are ready yet when it comes to a root zone roll-over. Though the majority of all resolvers are updated correctly, some users may experience nonfunctional websites from the 11th of October.
Why is the key roll-over so important?
DNSSEC technology was rapidly adopted. For example, more than 50% of all the .nl domains is secured with DNSSEC. That’s not surprising. DNSSEC prevents abuse on your brand or website by making DNS hijacking (redirecting visitors to a malicious server) impossible.
Part of the security of DNSSEC, and security in general, is that the cryptographic keys should not have a too long lifetime. The longer a key is in use, the more time malicious people have to compromise the key. And a compromised key compromises the security. The secured data cannot be trusted anymore.
The root zone key roll-over on the 11th of October addresses exaclty this risk. By inserting a new key in the root zone, any person trying to hack the key must start over again.
What will change on the 11th of October?
At this moment, the root zone is signed with the original KSK that was published in 2010. In July 2017, ICANN already published a second KSK in the root zone, but this key is not yet used to sign any zones. Exactly that is what will change in two weeks. From the 11th of October onwards, the new key will be used to sign the zones. The old key will remain in the zone for 3 more months before it will be revoked.
The below timeline by ICANN visualises this project:
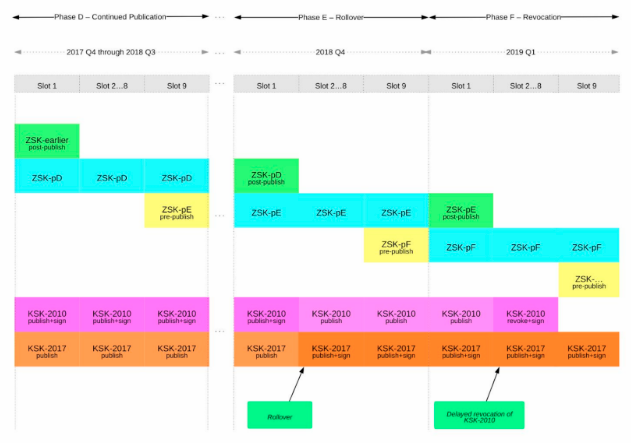
Why is there a risk?
Every DNS resolver that is capable of validating DNSSEC-secured domain names will eventually have to validate the root zone as well. Validation is a chained process. We have just published this new page in our knowledge base to tell you more about the validation process of DNSSEC.
So far, so good. Every DNS resolver knows the original key, the “KSK-2010” in the above chart. However, investigation shows that not all resolvers know the new key, the “KSK-2017” yet. This key has now been available for over 14 months. As soon as ICANN starts signing the zones with the new key, such resolvers will not be able to validate the results. Non-validated results will prevent the requested website from being loaded.
The original plan was to roll-over the key last year October. But because of above findings and the lack of impact analyses, it was postponed for a year.
Although still exact numbers are unknown, it’s estimated that “several million internet users globally” may be impacted.
If you run your own DNS resolver, ICANN’s KSK roll-over quick guide explains how you can check your configuration. It also tells you how to update it, in case the new key has not been imported automatically.
If you do not run your own resolver but still experience problems, you may want to contact your ISP to check if they are up-to-date. If, due to the key roll-over, your website is unavailable to some of your customers, you may want to disable DNSSEC temporarily as a quick fix.
Those interested in all details around the KSK roll-over may visit the special section on ICANN’s website.


