
Maintaining the security of our customers’ data has naturally been one of our top priorities over the years. Here, we would like to share what we have done for your password security and what you can do yourself to improve it.
Multiple layers of protection
Any system administrator knows it is a bad idea to store plain-text passwords. If a database containing plain-text passwords is compromised, user accounts are in immediate danger. To reduce this danger, only password hashes are stored in a database. Unfortunately, while this prevents the direct reading of passwords in case of an attack, the nature of hashing mechanisms allows attackers to brute force the hash offline.
Over the years, we have quietly upgraded our password hashing approach to stay current with industry standards. Our password storage scheme relies on a number of different cryptographic functions and protocols in layers. These include bcrypt with a per user salt and an HMAC implementation.
The value of bcrypt is that it is designed to be slow and hard to speed up via custom hardware and GPUs. HMACs strengthens the security of a plain hash function by adding a cryptographic key. This is why it is substantially less affected by collisions than their underlying hashing algorithms alone.
Best practices for users
However, having a robust cryptographic protocol for password storage is only part of the solution for protecting your data. A large amount of responsibility lies with you as a customer. Best practices for you to use on Openprovider include having a strong password and using two factor authentication.
To make sure our customers have strong passwords, we will send you an email reminder to change your password every 90 days. At any other time you can also change your password through your RCP by going to Accounts>Security>Password.
Secondly, we highly recommend you to use two factor authentication for all of your accounts. Most people only have one layer of security – their password – to protect their account. If you use two-factor authentication, a bad guy will need access to your phone to get into your account – making it a lot harder for him!
In order to activate two-factor authentication for an account, you need to:
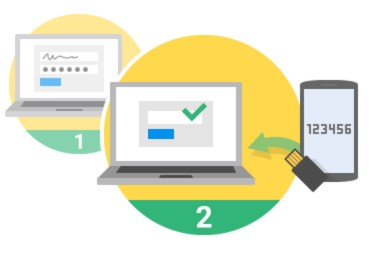
- Log in to the RCP and open Account>Security>Two Factor Authentication.
- Install the Google Authenticator app on your smartphone (documentation).
- Choose “Add account” and scan the QR code. If you cannot scan the code, choose “Manual entry” and enter the “Secret key” as shown below the QR code.
- Enter the verification code that you‘ll see on your smartphone into the box “Verification code” and press “Enable”.
From that moment on, our system will always ask you to verify your login attempt through Google Authenticator when logging in.


