If you’re incorporating email into your lead generation efforts, you should be aware that this medium can be vulnerable to manipulation. Hackers and social engineers are using dormant email addresses and abandoned or newly minted domains to trick email recipients. This increasingly common practice is called email spoofing.
How does someone spoof an email? And how are hackers possibly using your URL to spam and scam people you want to convert from leads to loyal customers? In this article, we are offering you a deeper insight into this practice and how you can prevent it.
What is email spoofing?
Spoofing is a broad term that covers several fraudulent practices that use email. Spoofed emails are often sent from external sources as unauthorized email to customers who haven’t requested information or opted-in to a subscriber list.
Spoofed emails can also be generated internally – or appear to come from someone within an organization – in spear phishing attempts. In spear phishing attempts, it appears to a receiver as if the email came from a trusted entity. Hackers do this in an effort to trick the recipient into giving the fake sender passwords or account numbers.
Spoofed emails either have a fictitious sender and a real email address, or they use a fake or abandoned address. This address then redirects the user to a landing page or allows the sender to insert malicious code into bad links. The perpetrators can also falsify the return-to and reply paths to redirect legitimate emails.
Unfortunately, some of the largest names in the email industry (such as Gmail, AOL, Yahoo, Microsoft, and Apple) have basically sold their customers out by allowing third-party access to email addresses to advertisers, government agencies, and probably spoofers as well. As many are realizing, the few bucks a month it costs to subscribe to a secure email platform that uses end-to-end encryption is fast becoming a no-brainer in the battle to beat the bad guys. If you haven’t been the victim of a spoofing or phishing attack yet, it’s likely just a matter of time. Truly secure email is a strong preventative first step.
How to spot a spoofed email?
Most of the time, you can spot a phony email if you know where to look and how they’re typically altered. If you suspect that an email comes from an imposter, you should compare certain details against a previous message that you know is legitimate. Is the sender’s address formatted the same? Are they asking for your password? Most companies won’t do that.
Check the email header
The best signs of fakery are in the header. Sometimes, the email will appear to come from someone you’ve had contact with before, but the URL will be different. Say, for example, that an email is sent to you from someone who’s supposedly a previous contact on LinkedIn. The URL in the email address would say that it isfrom contactname@linkedin.com. If the name of the sender in the URL is different, such as LinkedIn.com or it doesn’t have the name of the company in it at all, it’s a fake.
You can obtain a lot of information in the header, including the IP address of the sender. You can then even investigate this further through the Whois.
Check the company logo, name and URL
Another common gimmick is to claim that there’s a problem with your account, or you have a delivery waiting. Many people have received fake Amazon and DHL scam emails in the past. They usually provide a link to follow to login to your account, though are getting more clever with their methods all the time. If you’re foolish enough to do log in, you’ve just handed over the keys to that account.
Such emails may come from Twitter, Gmail, and PayPal as well. Some of them look pretty authentic at first glance. But you can see they usually copy/paste the real company logo or use one that’s similar but for a few minor details. The same goes for URLs and names.
Sometimes, the information in the email subject line, sender field, or body of the email is a blue embedded link. Mousing over it may reveal the true identity of the sender. Don’t respond to such emails or click on any links in it.
5 ways to mitigate email spoofing
In addition to using a secure email service that has high-level encryption, built-in spam filters and a range of email security tools, there are several ways you can protect your email account and contacts. You can do this using tools, security protocols, and a little bit of legwork.
- Establish a formal policy for email security. Work with a security consultant to create it, if need be.
- Create a security awareness training course for your company. Make sure that all current employees and new hires know your email policies.
- Create a Sender Policy Framework (SPF) that includes domain discovery, email services discovery, and validation.
- Adopt a Domain-based Message Authentication, Reporting & Conformance (DMARC) mechanism. This can prevent spoofing of transit-/SMTP-level(sender data) and content- MIME-level (headers). You can validate your protocol or setup by sending some test emails to see how it performs. The testing code should look similar to this: “Authentication-Results: spf=pass (sender IP is 5.6.7.8) smtp.mailfrom=example.astrix.co.uk; astrix.co.uk; dkim=pass (signature was verified) header.d=example.astrix.co.uk;astrix.co.uk; dmarc=pass action=none header.from=example.astrix.co.uk;compauth=pass reason=100”
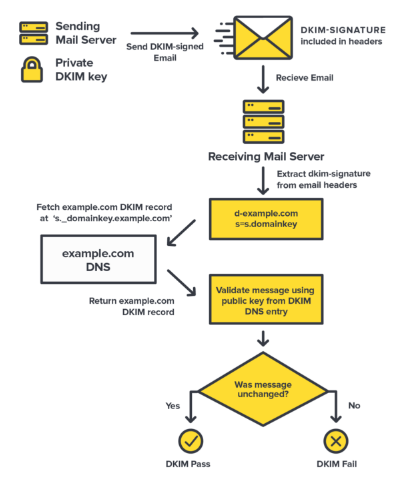
- Create and analyze forensics reporting based on your DMARC protocol and consistent monitoring. This tool makes it easy to accurately inspect DomainKeys Identified Mail (DKIM) records and validate them.
Protection also begins with how you handle your own email security. Modeling compliance and implementing best practices will allow you to lead your team by example. Create strong email passwords and safeguard them. The current industry standard is a combination of 12 characters, rather than the previous eight. Make sure not to use us words, phrases, or names that would be easy for a social engineer to guess or reverse engineer, like your pet’s name or your favorite song.
Final thoughts
Email is still one of the most effective ways to market your business and engage with your customer base. Using email security best practices will help keep you messages flowing to those who need and want them.
In addition to preventive measures you can take, most reputable email services provide the means for reporting suspected spam or phishing attempts. It’s worth the effort to secure your email address and retain your good domain name.
If you want to secure your email now you can try out the SpamExperts solution offered by Openprovider. With SpamExperts, your incoming mails will be safe. You can also add an extra layer of security by enabling sender checks via SFP, DKIM and DMARC in the configuration of your incoming filter (Incoming – Protection settings -> Filter settings).
If you register now, you’ll get one SpamExperts filter for free for your domain for 1 month. If you already have an account with us – just activate free SpamExperts filter promo by using the FREESPAMEXPERTS promo code on the dashboard of our control panel.


